
The Importance of Vulnerability Assessment and Penetration Testing (VAPT)
Outsourced penetration testing
enhances cybersecurity, uncovers overlooked weaknesses, and allows internal teams to focus on daily operations securely.
In today’s digital environment, cybersecurity threats are not just increasing in number—they’re evolving in sophistication. Regular vulnerability assessment and penetration testing are vital strategies for protecting your corporate network. These proactive security measures don’t just mitigate risks but also foster a security-aware culture within your organization.
Using an outside company for penetration and vulnerability testing provides an unbiased assessment and ensures that testing is conducted with the latest attack techniques and threat intelligence, often uncovering overlooked weaknesses that internal teams might miss. This approach also frees up internal resources, allowing IT staff to focus on daily security and operations while experts focus on identifying critical vulnerabilities.
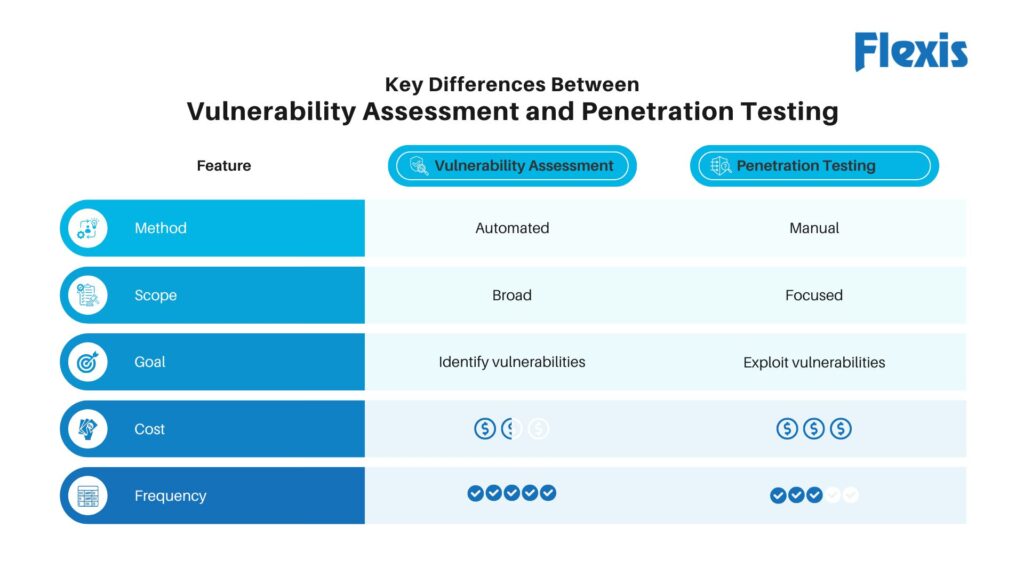
Vulnerability Assessment and Penetration Testing Explained
Vulnerability assessment is an automated, high-level process that regularly checks systems and networks for known weaknesses, missing security controls, and common misconfigurations. Its goal is to spot as many vulnerabilities as possible, making it ideal for frequent scans (weekly or monthly) and cost-effective. A typical example is using Nessus to detect outdated software versions.
On the other hand, Penetration testing is a hands-on, in-depth approach where security experts simulate real attacks to exploit vulnerabilities, showing the impact of potential breaches. Done annually, it provides a deeper look into security risks and is more costly but highly insightful. For instance, a consultant might test unauthorized access to highlight critical security gaps.
Here are the top reasons why regular vulnerability assessment and penetration testing should be part of your IT security plan.

1. Identify Vulnerabilities Before They’re Exploited
Vulnerability scans and penetration tests work together to detect and assess potential security weaknesses. A vulnerability scan examines your network for known security flaws, while a penetration test goes a step further by simulating real-world attacks to evaluate how an attacker could exploit these vulnerabilities. Running these checks regularly helps you stay one step ahead, identifying and addressing potential issues before they can be exploited by malicious actors.

2. Ensure Compliance with Industry Regulations
Organizations across various sectors are subject to stringent compliance standards, such as GDPR, HIPAA, and PCI-DSS, which mandate routine security assessments. Regular penetration tests and vulnerability scans demonstrate compliance with these standards, showing that your organization is committed to maintaining robust security practices. Many regulatory bodies require these assessments as proof of compliance, and failure to comply can lead to costly fines and legal consequences.

3. Reduce the Risk of Data Breaches
Data breaches can be catastrophic, leading to financial losses, reputational damage, and loss of customer trust. Regular testing helps you uncover vulnerabilities that could expose sensitive data. By promptly addressing these issues, you reduce the likelihood of unauthorized access and data theft, helping protect your company from potentially severe financial and reputational harm.

4. Optimize Your Security Investments
With the insights gained from penetration testing and vulnerability scans, you can make more informed decisions about your security investments. Testing results highlight specific vulnerabilities and weak spots, allowing you to allocate resources more effectively by focusing on areas that pose the most significant risk. Instead of investing in blanket security solutions, you can address vulnerabilities in a targeted and cost-effective way.

5. Improve Incident Response Capabilities
Penetration testing provides a valuable simulation of what a real-world attack would look like, giving your IT and security teams practical experience in responding to security incidents. These exercises expose gaps in your incident response strategy and allow your team to fine-tune their responses, improving their ability to detect, respond to, and recover from security events in real-time.

6. Foster a Security-First Culture
Regular security testing sends a clear message to your employees, stakeholders, and partners that cybersecurity is a top priority for your organization. By consistently assessing your network, you reinforce the importance of security and encourage a proactive, security-conscious mindset throughout your organization. This culture shift helps reduce human error, which remains one of the most common causes of data breaches.

7. Protect Your Brand’s Reputation
In today’s market, customers expect companies to keep their personal and financial information secure. Regular testing can help you maintain the trust of your clients by safeguarding their data and assuring them that your network is secure. A well-protected network minimizes the risk of a data breach, helping you avoid the negative publicity and customer attrition that often follow security incidents.

8. Adapt to an Evolving Threat Landscape
Cyber threats evolve rapidly, with new vulnerabilities and attack methods emerging constantly. Regular testing ensures that your security strategy adapts to these changes, making it easier to address emerging threats and vulnerabilities. With frequent updates to your security assessments, your organization is better equipped to respond to the latest security challenges.
Conclusion:
Routine vulnerability assessment and penetration testing aren’t just beneficial—they’re essential for modern businesses. By proactively identifying vulnerabilities, ensuring compliance, reducing data breach risks, and fostering a security-first culture, these practices help protect your corporate network from a wide array of potential threats. It is best to leverage an outside company for penetration and vulnerability testing to ensure an unbiased assessment leveraging the latest attack techniques and threat intelligence. This approach also frees up internal resources, allowing IT staff to focus on daily security and operations while experts focus on identifying critical vulnerabilities.
Incorporating regular security testing into your IT strategy enhances your organization’s resilience against cyber threats, strengthens your defenses, and ultimately supports long-term business success.
For more information on how you can benefit from penetration testing and vulnerability assessments, contact Flexis today.
Routine vulnerability assessment and penetration testing
strengthen defenses, ensure compliance, and free internal resources, enhancing business resilience.
Disclaimer: This post is for informational purposes only. Always consider your specific needs and consult with a professional to determine the best backup management strategy for your organization.


